
Comprehensive Vulnerability Assessment and Penetration Testing
Comprehensive Vulnerability Assessment and Penetration Testing
Identify and mitigate gaps and weak points in your cybersecurity infrastructure
Vulnerability assessment process involves the use of vulnerability assessment tools that identify vulnerabilities in your organization’s IT assets, which have the potential to be exploited by attackers. These are systemic flaws that can leave your organization exposed to both known and unknown threats such as ransomware and more.

What is insecure design?
What is insecure design?
Insecure design means the risks related to design and architectural flaws that are built-in right from the beginning of software development, if the appropriate security mitigations are not taken.

What is a Secure Code Review?
What is a Secure Code Review?
A code review validates the security standards of your web application source code and identifies the underlying security vulnerabilities which may have been ignored in the development phase and ultimately exposing your application weak points. This exposed application will prone to cyber-attacks. A secure code review is a remedial method that involves a series of manual and automated screening of your web application’s source code to find out the security vulnerabilities that may prevail.

What Is Security Misconfiguration?
What Is Security Misconfiguration?
Security misconfiguration occurs when security settings are not adequately defined in the configuration process or maintained and deployed with default settings. This might impact any layer of the application stack, cloud or network. Misconfigured clouds are a central cause of data breaches, costing organizations millions of dollars.
Vulnerabilities are generally introduced during configuration. Typical misconfiguration vulnerabilities occur with the use of the following:
- Defaults—including passwords, certificates and installation
- Deprecated protocols and encryption
- Open database instances
- Directory listing—this should not be enabled Error messages showing sensitive information Misconfigured cloud settings
- Unnecessary features—including pages, ports and command injection

Broken access control vulnerability
Broken access control vulnerability
Broken access control vulnerability is a type of security flaw that allows an unauthorized user access to restricted resources. By exploiting this vulnerability, attackers can circumvent standard security procedures and gain unauthorized access to sensitive information or systems.

WHAT IS COMMAND INECTION VULERABILITY?
WHAT IS COMMAND INECTION VULERABILITY?
Command injection is a cyber attack that involves executing arbitrary command on a host operating system(OS). Typically the threat actor injects the commands by exploiting an application vulnerability, such as insufficient input validation.
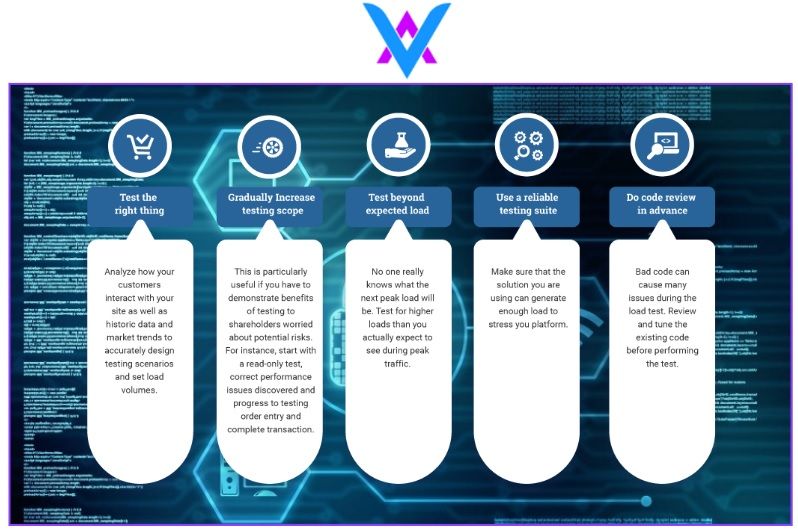
Secure code
Secure code
Secure code review is a manual or automated process that examines an application's source code. The goal of this examination is to identify any existing security flaws or vulnerabilities. Code review specifically looks for logic errors, examines spec implementation, and checks style guidelines, among other activities.
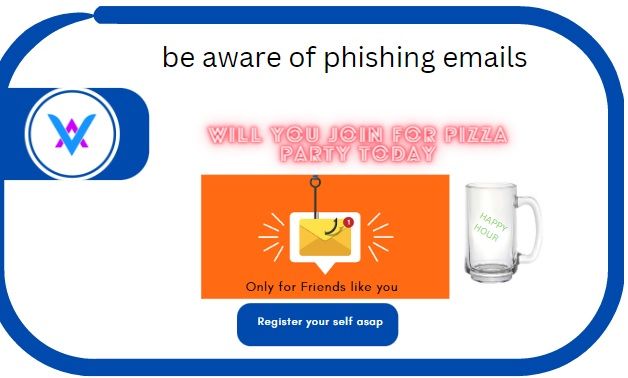
How Do Phishing Simulations Work?
How Do Phishing Simulations Work?
Phishing simulations are a bit like a phishing vaccine: to develop immunity to a virus, you administer a vaccine—a small dose of the virus—to teach the body how to combat it. To defend against phishing, you administer phishing simulations to teach your employees how to combat the threat.
The Benefits Of Phishing Simulation And Testing Prevent Data Breaches
This one speaks for itself, really. Simulated phishing emails teach your employees how to spot a phishing attack so that they won’t fall victim to a real one, should it find its way into their inboxes. This means that they’re far less likely to click on a malicious attachment or URL if they’ve learned to be suspicious of it.

Why is API security testing important?
Why is API security testing important?
At the most basic level, API security testing helps identify and prevent vulnerabilities and their associated potential organizational risk. Specifically, API security testing is fine-tuned to both the API being tested and an organization's overall strategy and best practices.
